In a world of data breaches, hacking and other cyber threats lurking at every corner, implementing some form of two/multi factor authentication should be a given within your organisation. Given the prevalence of cybercrime, any system that can filter legitimate users from malicious users should be embraced. However, over the years many forms of authentication have been developed. It is becoming increasingly harder to navigate which forms of authentication are right for your business.
Today, we will dive into some of the most popular forms of authentication provider by Managed IT Services. We’ll not only look at what types of authentications are out there but also what their strengths and weaknesses are too.
What is authentication?
Authentication is simply the act of adding an extra layer of security onto your accounts. Say in the case your password was leaked, guessed or stolen, a hacker cannot just simply log into your account without authenticating themselves. Thus, stopping any real damage occurring before a hacker even has a chance to get in. Just about anything can be protected with authentication, bank accounts, emails, laptops, social media… the list goes on.
Authenticator Apps
Perhaps the most popular and safe method of authenticating is using an app. Popular apps include Google Authenticate, Microsoft Authenticator and DUO Mobile. Authenticator apps generally work by prompting you to confirm your login via the app or enter a time-based one-time password/code (TOTP). Authenticator apps are easy to use and accessible to most people with a smartphone. They also generally use a standardised algorithm. This means that just about any authenticator app will work with whichever account you’re looking to protect.
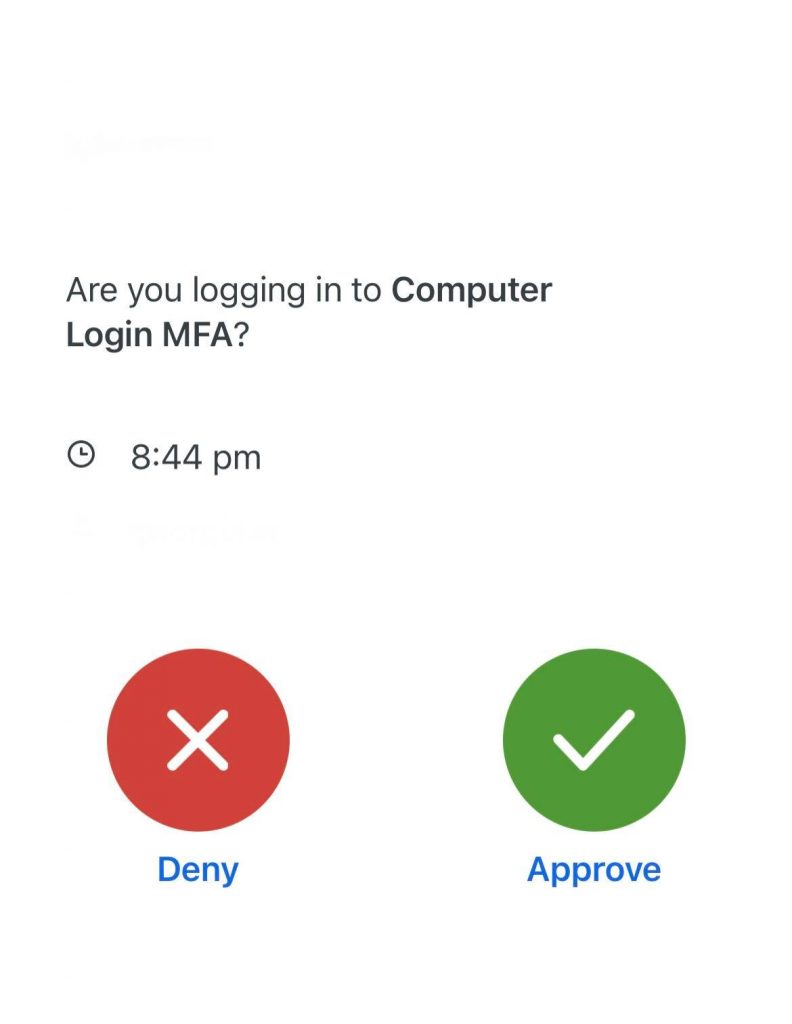
Cons?
Whilst the most popular and safe method of authenticating, authenticator apps aren’t without their flaws. If you lose your phone or cannot access it again in some way and the proper settings haven’t been configured, it can be a very arduous process to get back into authenticated accounts. This can be avoided by just making sure back-up settings are configured in the app of your choice. Secondly, like everything else in the world of technology, authenticator apps are also subject to security breaches. Just last week, Okta Verify confirmed they suffered a data breach.
PKI Card
A PKI card, or Public Key Infrastructure card, is another popular authentication tactic. This type of authentication is popular in larger businesses and corporations. A user is given a smart card with a chip that is inserted into their computer. Upon insertion, a pin set by the user is requested as well as the password to the laptop. Even if someone knows the laptops password, if they do not know the pin generally they cannot access files, emails or even the internet.
Cons?
Whilst sometimes the safest storage for passwords and authentication is actually physical and not digital assets, PKI cards also have cons. PKI cards can be expensive, costing hundreds and sometimes even thousands of dollars per card. They can also easily break, get lost or fall into the wrong hands. Therefore, whilst they’re nifty and can feel safer due to their physicality, PKI cards also come with their own set of issues.
SMS Authentication
Whilst SMS authentication is likely the most widespread and easy form of authentication, majority of tech experts (including us here at Milnsbridge) do not recommend this. SMS authentication works by logging into an account that is protected by two-factor authentication. Upon entering the password, a short code will be texted to you. In turn, you enter this code to verify it is indeed you.
This sounds like it would be a secure way of authenticating, because its your mobile number after all isn’t it?
Not quite, SMS authentication has several flaws:
- Anyone in person can read these codes from your phone
- SIM cards can be removed and inserted into another phone, along with your SMS’ and authentication texts
- Through a series of shady dealings, impersonation and cunningness, it is actually possible for hackers to go to the extent of posing as you to your telco provider and arranging for a replacement SIM to be sent to them, unbeknownst to you. Then, all of your authentication texts can appear on this replacement SIM.
- Even without having to go to the above effort, due to exposed weaknesses, SMS’ carrying OTP’s (One Time Passcodes) can easily be intercepted.
It is these flaws that makes SMS authentication the most dangerous and vulnerable form of authenticating an account.
IT security should be at the forefront of every business owner’s mind. Human error and the prevalence of cyber attacks are too pervasive to leave security up to chance. Authentication is a relatively painless way to add an extra layer of security to your accounts that are worth protecting. And in a market when you’re spoiled for choice, it is important to know the different types of authentications.
If you’d like to talk more about the ways Managed Security and MSP Services can benefit your business, call Milnsbridge today on 1300 300 293.
